Connecting devices and systems to improve efficiency and gain important insights has revolutionized how we interact with technology. The number of connected IoT devices had increased by 16.7 billion in 2023, according to a new IoT review. Also, it was noted that the EU had the power to create the Network and Information Security Directive. A tactical approach that combines cutting-edge technology with meticulous planning and execution is necessary to create a successful IoT product.
In this article, we’ll look at the best methods for creating an IoT product to ensure a smooth and trustworthy user experience. By the end of 2025, the number of installed IoT devices will total 27 billion, which includes everything from consumer-level gadgets to businessIoT. Examples include health IoT devices for personal healthcare to global health providers, and IoT devices in smart home applications for energy efficiency and security. IoT devices significantly increase the security and safety of miners in both underwater mining and in agriculture. The idea of online twins has been used in numerous large-scale coal mining projects. For developing IoT applications and services, we must adopt a comprehensive software engineering IoT framework, as illustrated in Illustration 1.
One of the best ways to create IoT devices is to identify distinct requirements and features. The procedure is as follows:
- Start with a clear problem statement and user requirements using sysSQUARE ( the SEI’s fundamental SQUARE requirements methodology was created ).
- Create a prototype and regularly test it
- Choose the appropriate hardware and software components.
- Follow the laws and standards for security and IoT connectivity.
- Optimize the device’s performance and power consumption.
- Design for interoperability and scalability
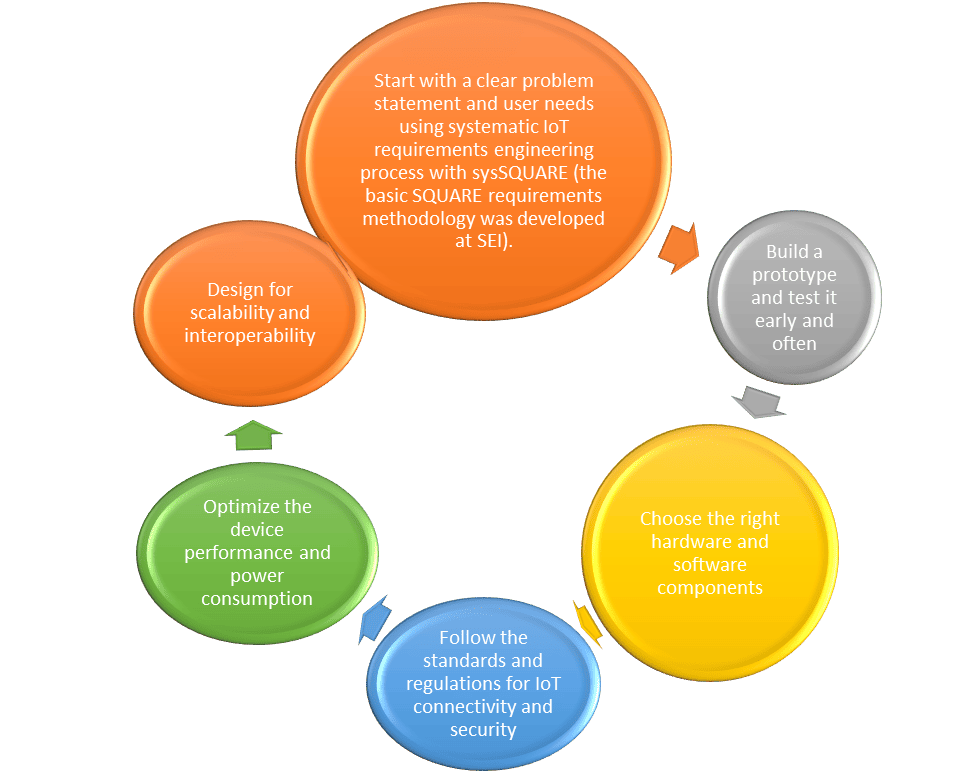
Illustration 1 – Software Engineering Framework for Cyber-Physical and IoT Systems.
Next, it’s time to create IoT applications that are tailored to a particular need, such as smart homes, mining, smart cities, bright environments, and smart transportation. The procedure for creating software engineering typically follows:
- Using the sysSQUARE methodology, define the device requirements and specifications.
- Select the appropriate framework and development platform ( SEF-IoT ).
- Implement the device’s logic and functionality.
- Integrate the device with data analytics and cloud services.
- Troubleshoot and debug the device problems
- Install and update the device’s firmware
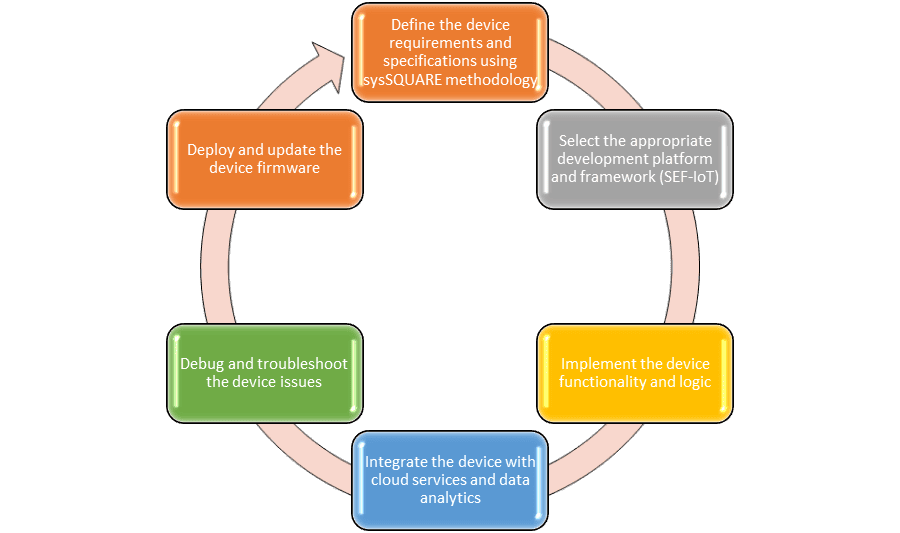
Illustration 2 – IoT- Edge Applications Development Lifecycle
Adopting Rigorous Approaches for IoT-Edge Application Development
It is crucial to adopt a rigorous approach and best practices for IoT- Edge application development, as illustrated in Illustration 2. This includes a number of well-known methods, including Security by Design, which codifies the idea of incorporating security considerations from requirements to design, implementation, and testing. This procedure is also known as” Bound-In Security.” Use user encryption when sending and receiving data. Implement device authentication and safe boot processes. Also, regularly update software to provide a mechanism for over-the-air updates that address security flaws and improve functionality. To prevent tampering, make sure that updates are signed, authenticated, and encrypted.
Best Practices for Robust IoT Product Development
The second-best practice is data privacy, which supports a crystal-clear and obvious definition of the data that the device collects. In accordance with privacy laws, obtain obvious user consent, limit data collection to what is simply required for the device’s functionality, and encrypt sensitive data.
The next best practice is to design for interoperability and standards, and to adhere to industry standards to improve interoperability with other hardware and software. Use commonly accepted communication protocols to facilitate integration.
Designing for optimal power consumption is the third best practice. Supporting UN sustainability objectives, especially Goal 7: Affordable and Clean Energy, is one of the most crucial best practices. This involves improving power consumption by increasing the device’s battery life, implementing sleep modes, and other power-saving features when the device isn’t in use.
Designing for scalability is the second best practice, which takes into account potential increases in the number of devices and the data they generate. It is accomplished by designing devices to scale with growing demands.
User-Friendly Interfaces are among the fifth best practices, which help to make the setup and configuration process user-friendly. Provide users with apparent documentation and support for fixing common issues.
The seventh best practice emphasizes the design of IoT-edge computing, including using edge computing to process data locally, reducing reliance on cloud services, strengthening these edge nodes ( such as edge gateways, edge servers, edge computing ), security, and taking into account the use of edge analytics to reduce latency and improve real-time decision-making.
The eight best practices include designing for reliability and redundancy, including redundancy and failover mechanisms to improve reliability, and conducting thorough testing for different scenarios, including network disruptions.
The eighth best practice is necessary to adopt strict compliance with laws, staying informed about them, and adhering to provincial and industry-specific laws. Depending on the target markets, consider certifications like CE, FCC, or other.
The eighth and most important best practice is one that focuses on supply chain security, ensuring the security of the entire supply chain to prevent tampering or unauthorised access while manufacturing. Use reliable suppliers and verify the authenticity of the components.
Constant monitoring and diagnostics, as well as the implementation of precise monitoring tools to identify unusual behavior and potential security threats, are the eleventh best practices. To facilitate troubleshooting and debugging, this should include medical tools.
The last and final best practices revolve around making final decisions about how to handle the device’s end of life, making plans for how to end it, and ensuring the safe disposal of hardware and data.
Manufacturers can develop more stable, trustworthy, and powerful IoT devices that meet user expectations and regulatory requirements by adhering to these best practices.
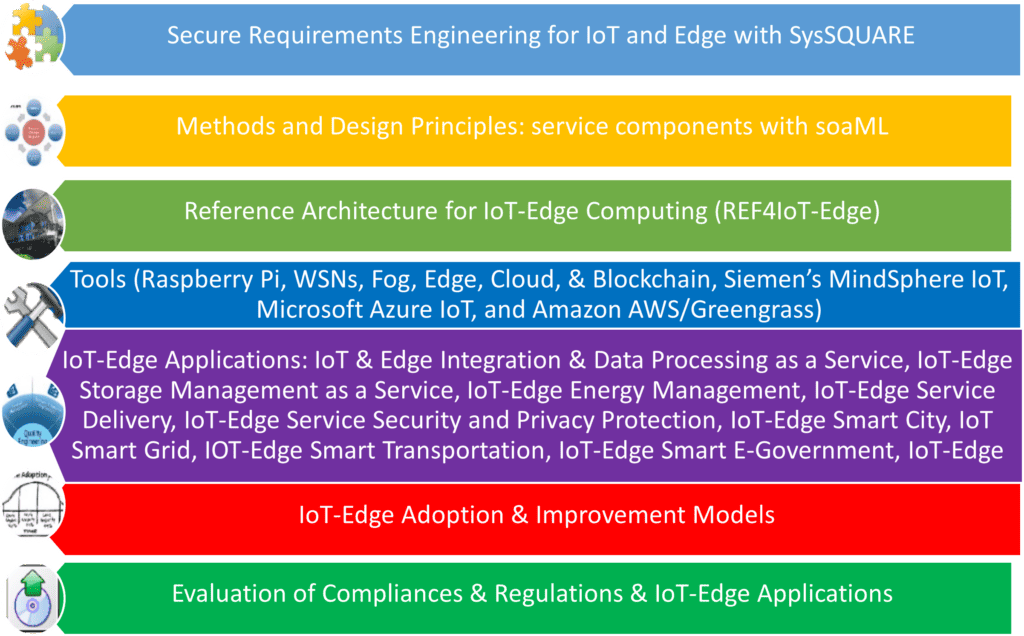
Illustration 3 – Safe Software Engineering IoT- Edge Framework.
Framework for Stable Software Engineering IoT-Edge Paradigm
Illustration 3 provides a comprehensive framework for the stable software engineering IoT-Edge paradigm, which begins with the evaluation of existing business strategies and best practices before gradually improving by adopting the twelve best practices that are described in this article.
A comprehensive approach is necessary to create a powerful IoT product that includes clear goals, solid security, effective power management, interoperability, user-friendly design, and scalability. By adhering to these best practices, you can make sure that your IoT product not only meets the needs of the current market but also provides the foundation for advancing in the rapidly-changing field of attached devices.